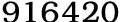|
|
 |
 |
|
Certification Validation and Checking Procedures by christy Lee
 |

|
|
Certification Validation and Checking Procedures |
|
|
|
|
|
Advertising,Business News,Computers
|
 |
|
When certificates are used for authentication, it is important that MCP certification validation and revocation checking is enabled. When IAS is the RADIUS server, Windows XP is the client, and certificates are used, the following certificate validation and checking procedures are followed: 1.IAS checks client certificates for valid dates. to see whether it is possible to construct a certificate chain. if configured, for required key usages and application policies present in the certificate. to ensure they have been signed with the client's private key. Q to check for revocation. 2.Windows XP checks the server certificate for valid dates. to see whether it is possible to construct a certificate chain. for required key usages in the certificate. to ensure the certificate has been signed with the server's private key. During authentication, Windows XP cannot check the revocation status of the IAS server certificate because network access is not available during EAP-TLS authentication. You can, however, enable an extra certificate check. You can explicitly select the trusted root CAs to which the server certificate can chain. This process will produce a trust decision prompt to users. While properly making a trust 70-270 decision might seem inconsequential, it is sometimes a difficult issue for end users. Management of the list can be provided by using update string values on WLAN clients through Active Directory directory services wire-less network policies. This solution might not be warranted except in high security situa?tions because of the need for user training and the potential management details involved in constantly updating the list. Key Management Key management is the process of key change and distribution. One of the failings of 802.11 wireless networks is that there is no key management. By default in 802.11 wireless networks, encryption keys are manually recorded in access points and clients. To change the keys, a new key must be entered both at the access point and on every client—an operation that is merely tedious when there are a few clients but near impossible with any frequency when there are many clients. The lack of key manage?ment is answered in 802.Ix by dynamic key assignment. Dynamic key assignment means that encryption keys are distributed to the clients automatically; it is not necessary to manually enter keys. Keys can also be frequently changed without manual intervention. Frequent key changes improves security because it makes it more difficult to crack the key and limits the harm done if an attacker deduces a key. Ideally, keys should be changed before any cracking tool can deduce them. Simply put, if the keys are changed often enough, an attacker will not be able to capture enough free exam question papers information in time to crack the encryption keys. Before he can do so, they will be changed.
Related Articles -
MCP certification, 70-270, free exam question papers,
|
Rate This Article  |
|
|
 |
|
|
Do you Agree or Disagree? Have a Comment? POST IT!
| Reader Opinions |
|
|
 |
|
|
|
 |
 |
 |
| Author Login |
|
|
 |
Advertiser Login
ADVERTISE HERE NOW!
Limited Time $60 Offer!
90 Days-1.5 Million Views



 |
 |
GENE MYERS

Author of four books and two screenplays; frequent magazine contributor. I have four other books "in...more
|
 |
 |
 |
 |
TIM FAY

After 60-plus years of living, I am just trying to pass down some of the information that I have lea...more
|
 |
 |
 |
 |
ADRIAN JOELE

I have been involved in nutrition and weight management for over 12 years and I like to share my kn...more
|
 |
 |
 |
 |
LAURA JEEVES

At LeadGenerators, we specialise in content-led Online Marketing Strategies for our clients in the t...more
|
 |
 |
 |
 |
MICHAEL BRESCIANI

Rev Bresciani is the author of two Christian books. One book is an important and concisely written b...more
|
 |
 |
 |
 |
STEPHEN BYE

Steve Bye is currently a fiction writer, who published his first novel, ‘Looking Forward Through the...more
|
 |
 |
 |
 |
LEVAL AINAH

I am an internet marketer and also an educator. My goal is to help others who are looking to improve...more
|
 |
 |
 |
 |
PAUL PHILIPS

For more articles, blog messages & videos and a free e-book download go to www.NewParadigm.ws your p...more
|
 |
 |
 |
 |
ALEX BELSEY

I am the editor of QUAY Magazine, a B2B publication based in the South West of the UK. I am also the...more
|
 |
 |
|