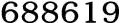Reading a commentary article, the author began to change on the understanding of the online banking. You may want to know why.
In " Hacker Defeat the security protection of two-factor "in, revealing a serious security problem. The article points out, the network Crime Behavior has begun to become very complicated. In fact, crime software (crimeware) is the new term used to describe their results.
Crime software According to Wikipedia's explanation, the software is a crime to steal your personal information to online banking for automatic unfair to steal from the criminal acts of money made for the purpose of malicious software.
"Criminal software (as distinct from spyware, Advertisement Software and malicious software) is designed (through social engineering or stealth technology) are used for identification Theft Activities in order to obtain computer users on the online banking and online retail business accounts, and transactions by unauthorized access to funds from these accounts or complete Theft Acts of crime control software. "
50 I have been thinking California led to a building Company Fermat 447 thousand U.S. dollars stolen cause of the event. To avoid confusion, first of all I must say that after the incident, forensic computer Expert After Fermat use technical analysis to determine a computer is infected with undisclosed criminal software. Clearly, infections occur in visiting a site. The following is the process of infection:
1, a Fermat employees logged on to Internet banking account.
2, site contains six numbers by one-time code for secondary verification.
3, the authentication is passed, the staff began to pay.
4, at the same time, the transfer of criminal software through 27 total 447 thousand U.S. dollars to the transfer of funds to other accounts.
Seems, in this case the software does not monitor the existence of the crime. I do not doubt that, if the code is valid, it can determine that the account was 44.7 million limit, and transfer control to the amount of the transaction.
Many factors Certification Reports on the incident, some people think that this is a multi-factor authentication mode failures. I do not agree with this view. Multi-factor authentication model has forced the network to extend the front to get criminals account connected. There are problems here, the bad guys once again found a workaround.
Solutions Experts offer a variety of solutions to strengthen the existing system. Here are some examples:
² establishment of a banking portal site can only be used to access a special terminal.
² users logged on to banking transactions portal in time, the use of one-time password to confirm each transaction.
² out of online banking in the user time, use the reCAPTCHA to confirm each transfer.
The real key In my view, these solutions are not focused. This computer has been infected, all known risk may emerge. Otherwise, the crime would not have happened. We are back to the old problem, trying to lead the bad guys. Well, actually more like the real situation is to catch up with them.
My solution For online credit card transactions, every business I chose to use one-time password. However, this new crime, because they do not know how powerful the software, so my methods may also be at risk.
My bank does not use a true multi-factor authentication mode. They believe that safety is a secondary factor, but they are not. I will be reminded of approved transactions, but not a one-time password restrictions. So my security authentication process is not as Fermat's bank.
I plan to from now on, use the LiveCD environment to deal with any form of online banking or retail transactions. In this way, I can ensure that the operating system is not compromised. This is a painful decision, but at the present time, I do not think there is no other effective solutions.
End of
The final analysis, the confidence of the computer led to the prevalence of malicious software. I do not want to take a risk. If you have a better solution, please let me know. I am an expert from China Toys Suppliers, usually analyzes all kind of industries situation, such as edison phonograph , tin litho.
Related Articles -
edison phonograph, tin litho,
|